Regardless of your motivations (attacker or defender), you need to know the ports, hosts and services available within a network.
From a defender’s point of view, the task is a precondition of several keys procedure:
- Asset Management – whoever manages the infrastructure (and its security) must know which devices are active and present within our infrastructure. Furthermore, it helps to detect unauthorized hosts that could derive from malicious activities (or more commonly, your system administrators forgot to document them… and maybe to apply the company’s hardenization procedures).
- Network scanning is a fundamental step of a company vulnerability management procedure. Here is a non-comprehensive list of its possible benefits:
- it allows the detection of unauthorized services and the presence of obsolete systems;
- it helps to verify the correspondence between the specifications document and the actual implementation;
- it helps to verify the correct application of the hardening procedures.
- Penetration test – independently from the approach in use, it is necessary to determine the active hosts and the exposed services. You have to do it even in a white-box penetration test to confirm your client/colleagues inputs.
From an attacker point of view… Well, that goes without saying
The network scanning procedure aims to identify active hosts. On the other hand, port scanning seeks to detect the ports that hosts disclose and with which it is possible to interact. Starting from the output of a network/port scanning, an attacker, or a newly hired CISO, can outline different traits of a company security posture.
In these articles we will see:
- the different steps of a network scan;
- some examples with the NMAP tool.
Host discovery
Port scanning involves sending several packets to the host and verifying its response. Usually, the analysis is restricted to the 1024 most common ports (it depends on the available time and the final goal of the analysis). As you may expect, performing this task for all the hosts within a network/infrastructure is time-expensive and generates a lot of noise.
In most cases, only a tiny fraction of IP addresses are active at any given moment. To avoid wasting time, the tester first perform the host discovery phase to determine the active hosts in the tested networks and infrastructure.
There are several techniques:
- ARP Ping scan;
- ICMP Ping scan;
- UDP Ping Scan;
- TCP SYN/ACK Ping scan;
- IP Protocol Ping scan.
As stated in the official documentation, the default NMAP host discovery strategy involves sending an ICMP echo request (-PE), a TCP SYN segment to port 443 (-PS443), a TCP ACK segment to port 80 (-PA80), and an ICMP timestamp request (-PP).
ARP ping scans are the most effective method to detect active hosts inside a LAN. Its limits are the impossibility of applying the technique on the subnet to which it does not belong. Even if you supply other -P* options to NMAP, the tool performs by default an ARP/Neighbor Discovery against targets on a local Ethernet network since it is the fastest and more reliable technique.
An ICMP scan consists of sending ICMP echo requests to hosts on the network. If a host is found to be active, it will return an ICMP echo response. The technique has limited usability as blocking ICMP requests is part of firewalls and systems’ basic hardening rules.
A TCP scan consists in sending TCP segment to the hosts and analysing the host response. There are two different modes: TCP SYN Ping scan and TCP ACK Ping Scan.
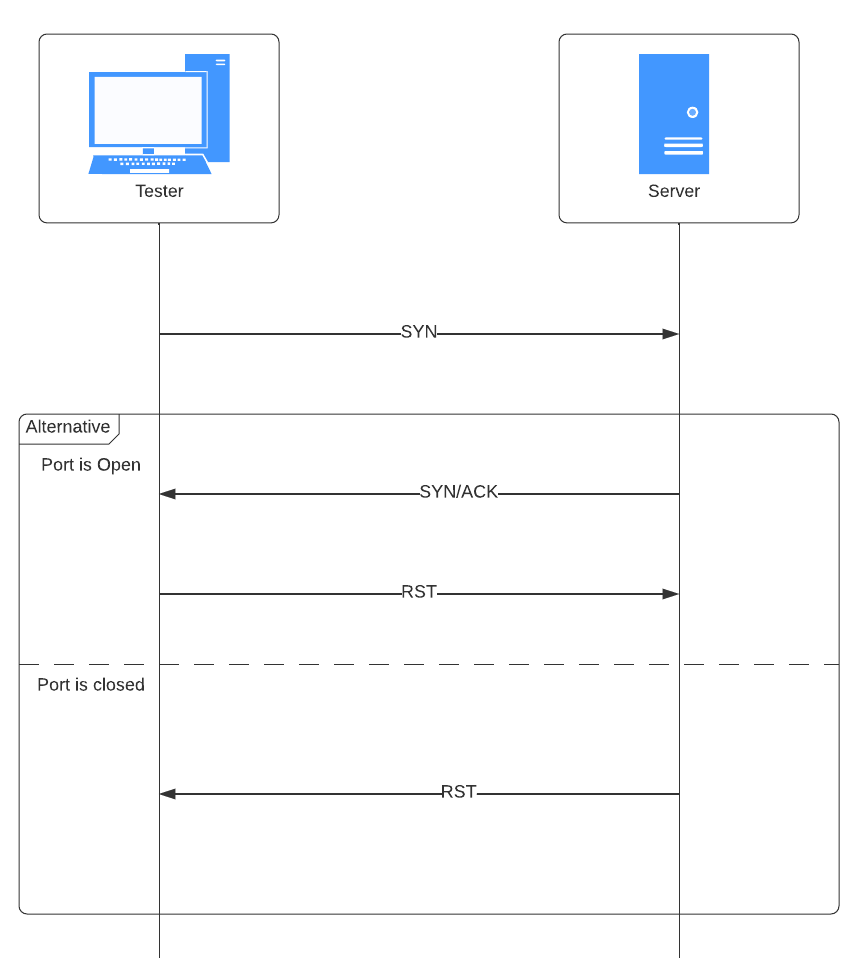
As illustrated in the figure, a TCP Syn ping scan consists of the following steps:
- The tester sends a TCP SYN segment to port 80.
- If the port is closed, the host responds with an RST segment.
- If the port is open, the host responds with a TCP SYN/ACK segment indicating that a connection can be established.
- Afterwards, an RST segment is sent to reset this connection.
Since it is a normal attempt to establish a TCP connection, traffic is not blocked by firewalls and does not require administrator permissions.
A TCP ACK ping scan instead consists of the following steps:
- The tester sends an empty TCP segment with the ACK flag set to port 80 (the nmap default port, but another port can be used).
- If the host is offline, it should not respond to this request.
- Otherwise, it will return an RST segment and will be treated as online. An RST is sent because the TCP ACK is not associated with any valid existing connection.
ACK Ping Scan requires administrator privileges. Since it is recognized and blocked by a stateful firewall, its main goal is to get information about the filter configurations, not port status.
Port Scan
Once the active hosts within a network have been determined, a portscan can be performed to determine exposed ports and services.
Several techniques are available:
- TCP Scan (Connect and Half Open Scan);
- UDP Scanning;
- SCTP Scanning;
- SSDP Scanning.
Only the first two strategies will be considered. Please see the NMAP manual for additional information on SCTP and SSDP Scanning.
TCP Scan
With a TCP Connect scan, a TCP connection is established with the host. That is, the whole 3-way handshake is performed.
The least expensive and most performing variant, the TCP Half Open scan (TCP SYN Scan) sends the SYN segment. If an open SYN+ACK segment is received, the port will be identified as open. In case of RST, the door will be judged closed.
A third typology, foresees the TCP FIN, NULL and Xmas Scans, foresees the modification of the flags of the TCP segment (FIN, URG, PSH, NULL) in an attempt to induce a response from the server.
The technical functionality exclusively on operating systems with implementations of the TCP/IP suite compliant with RFC793. For example, it does not work with Windows systems as these return an RST in both cases.
THE SEGMENT IS COMING
If the state is CLOSED (i.e., TCB does not exist), then all data in the incoming segment is deleted. An on the way the segment containing an RST is deleted. An incoming segment no containing an RST causes an RST to be sent in response. The confirmation and sequence field values are selected to render the recovery sequence acceptable to the TCP that sent the error segment.
RFC793
If the port is open, the system will not produce any while the response will return an RST/ACK segment if it is closed.
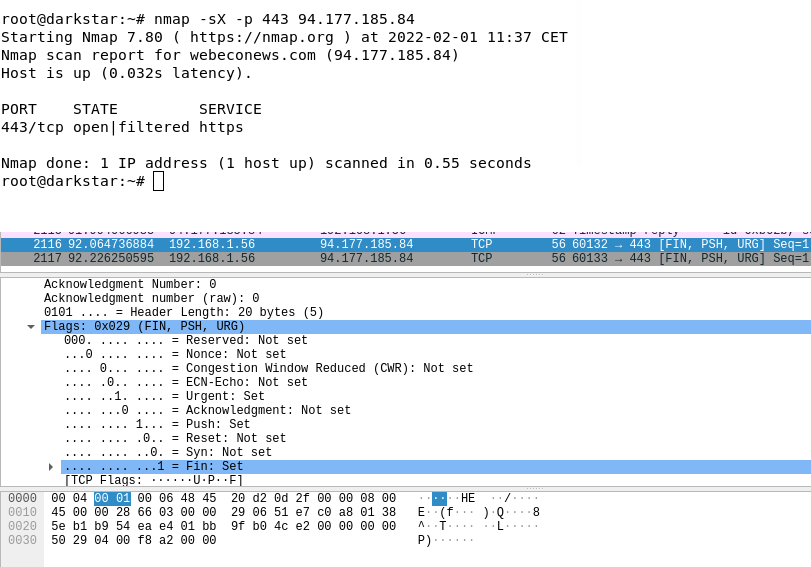
To understand the origin of the name, just look at the image below. Nmap’s -sX flag “Sets the FIN, PSH, and URG flags, illuminating the package like a Christmas tree.”
UDP scan
UDP connection does not involve a handshake. If a UDP packet is sent to a port on which no service is listening, the system will respond with an ICMP Port Unreachable. In case of no answer, the port can be considered closed or filtered.
Contermeasures
To detect and prevent network scanning attempts, we suggest the following countermeasures:
- carefully design your services to reduce your attack surface; exposing only necessary services and always keep in mind the principles of least privileges and need to know.
- Configure your firewalls to block all traffic that has not got a business justifications;
- Periodic reviews your firewall ruleset to keep it aligned to your business needs;
- Harden your servers, disabling all unused services;
- Perform network and port scans to ensure your firewall/server policies are aligned to your business needs.
- Configure an IDS/IPS to promptly detect network and port scans.
More Stories
CVE-2021-33621: A Critical Security Vulnerability in Ruby’s CGI
A critical security vulnerability, known as CVE-2021-33621, has been discovered in Ruby's Common Gateway Interface (CGI) that could potentially put...
Understanding and Mitigating the CVE-2022-41741 Vulnerability in NGINX
NGINX, a widely-used open-source web server, has recently been affected by a critical vulnerability - CVE-2022-41741. The vulnerability is specific...
The Most Dangerous Vulnerabilities in Apache Tomcat and How to Protect Against Them
Apache Tomcat is an open-source web server and servlet container that is widely used in enterprise environments to run Java...
ZDI-CAN-18333: A Critical Zero-Day Vulnerability in Microsoft Windows
Zero-day vulnerabilities are a serious threat to cybersecurity, as they can be exploited by malicious actors to gain unauthorized access...
CVE-2020-36518: A Critical Vulnerability in SolarWinds Orion Platform
The discovery of vulnerabilities in popular software can have far-reaching implications for cybersecurity. One such vulnerability is CVE-2020-36518, a critical...
Uncovering ZDI-22-1021: A Critical Zero-Day Vulnerability in Google Chrome
Zero-day vulnerabilities are a serious threat to cybersecurity, as they can be exploited by malicious actors to gain unauthorized access...

