Why metrics are crucial to proving cybersecurity programs’ value
As solutions to managing cybersecurity threats increase, surprisingly few metrics are available on how well these methods work to secure organizational assets. The National Institute...
Why authentication is still the CISO’s biggest headache
Authentication remains one of the most painstaking challenges faced by CISOs in organizations large and small. This longstanding, fundamental element of security continues to cause...
4 ways attackers target humans to gain network access
Every day, I see the failure in our technology. I’m sure you see it as well. Since the day we started receiving email, we have...
Log4Shell Used in a Third of Malware Infections
Software supply chain attacks realize researchers' worst fears Read More
Attackers Steal $618m From Crypto Firm
Cyber-heist could be biggest ever recorded Read More
What is Shodan? The search engine for everything on the internet
Shodan is a search engine for everything on the internet — web cams, water treatment facilities, yachts, medical devices, traffic lights, wind turbines, license plate...
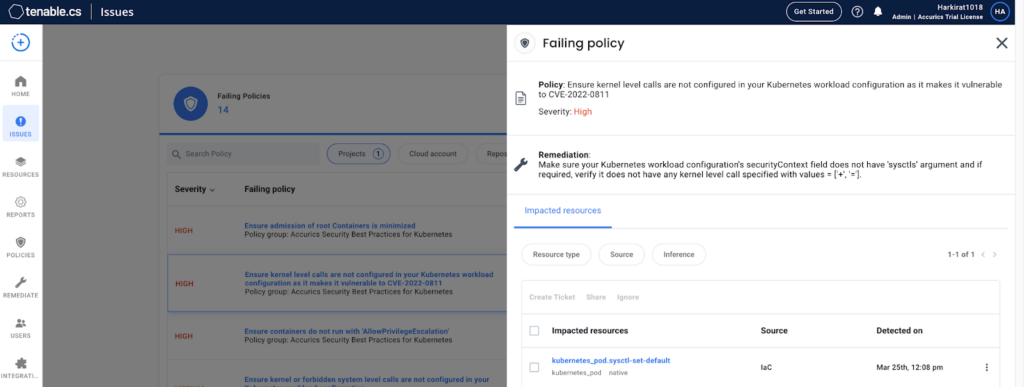
Cr8escape: How Tenable Can Help (CVE-2022-0811)
CrowdStrike discloses container escape vulnerability affecting CRI-O for Kubernetes. Here’s how Tenable.cs can help you detect vulnerable pods. Background On March 15, CrowdStrike published technical...
Personal Data of 620 FSB Officers Published Online
Ukrainian Directorate of Intelligence shares personal data of Russian agents Read More
Yandex is Sending iOS Users’ Data to Russia
Researcher claims Russian tech company is sending data harvested from iOS app users to Russia Read More
82% of Public Sector Applications Contain Security Flaws
The researchers also found the public sector takes twice as long to fix flaws once detected compared to other industries Read More