Apple and Google Turn Off Map Features to Help Ukraine
Tech giants also follow Meta in cracking down on Kremlin propaganda Read More
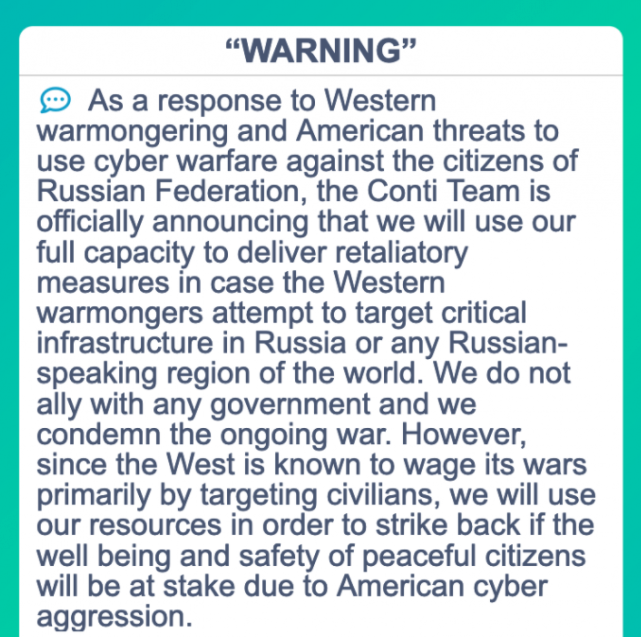
Conti Ransomware Group Diaries, Part I: Evasion
A Ukrainian security researcher this week leaked several years of internal chat logs and other sensitive data tied to Conti, an aggressive and ruthless Russian...
NIST Seeks Cybersecurity Framework Feedback
Institute wants to know how it can improve critical infrastructure cybersecurity framework Read More
Viasat Attributes Outage to “Cyber Event”
Disruption of satellite internet service in Ukraine and Europe began on day one of Russian invasion Read More
State Bar of California Investigates Data Breach
Probe launched after 260K confidential attorney discipline records leaked online Read More
Eugene Kaspersky’s Statement Provokes Controversy Within Cybersecurity Industry
Eugene Kaspersky's statement on ongoing conflict in Ukraine provoked strong reaction from leading cybersecurity figures Read More
Analyzing Cyber and Influence Operations in the Russia-Ukraine Conflict
The Russian invasion of Ukraine represents a new type of warfare, including extensive cyber and information operations Read More
Rash of hacktivism incidents accompany Russia’s invasion of Ukraine
In keeping with the hybrid nature of Russia’s invasion of Ukraine, several hacktivist groups and hackers have joined the fight in the embattled nation, including...
Decrypting Hive Ransomware Data
Nice piece of research: Abstract: Among the many types of malicious codes, ransomware poses a major threat. Ransomware encrypts data and demands a ransom in...
Why client-side web application security is critical to protecting from Magecart and other similar attacks
What can’t you buy on the internet? Last-minute birthday gifts. Check. A new refrigerator. Check. An engagement ring. Check. Groceries. Check. Travel to foreign lands....