Google Researchers Claim First Vulnerability Found Using AI
The flaw, an exploitable stack buffer underflow in SQLite, was found by Google’s Big Sleep team using a large language model (LLM) Read More
US Says Russia Behind Fake Haitian Voters Video
US government agencies said the video, widely shared on social media, is part of Russia’s broader strategy of undermining the integrity of the Presidential Election...
Sophos Versus the Chinese Hackers
Really interesting story of Sophos’s five-year war against Chinese hackers. Read More
Supply Chain Attack Uses Smart Contracts for C2 Ops
Checkmarx has observed a novel npm supply chain attack using Ethereum smart contracts to manage command-and-control (C2) operations Read More
UK Council Sites Recover Following Russian DDoS Blitz
Several UK council websites are back online after being disrupted by Russian hacktivist DDoS attacks Read More
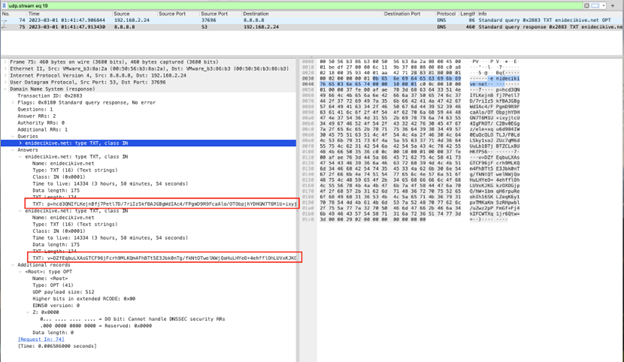
Ngioweb Remains Active 7 Years Later
Executive Summary Seven years after its first appearance, the proxy server botnet Ngioweb continues its impactful presence on the internet with barely any relevant changes...
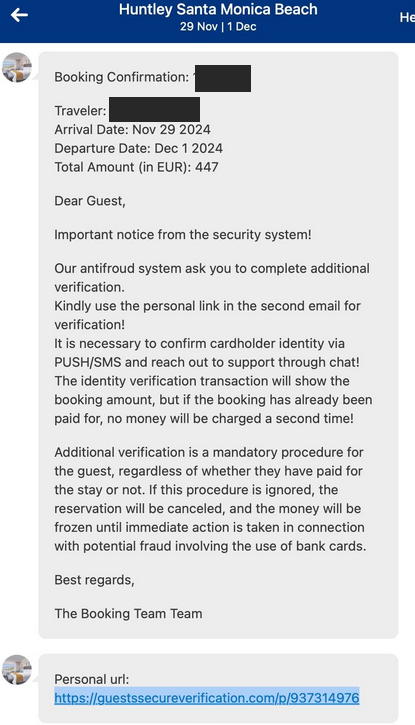
Booking.com Phishers May Leave You With Reservations
A number of cybercriminal innovations are making it easier for scammers to cash in on your upcoming travel plans. This story examines a recent spear-phishing...
Friday Squid Blogging: Squid Sculpture in Massachusetts Building
Great blow-up sculpture. Blog moderation policy. Read More
Ngioweb Remains Active 7 Years Later
Executive Summary Seven years after its first appearance, the proxy server botnet Ngioweb continues its impactful presence on the internet with barely any relevant changes...
Sophos Warns Chinese Hackers Are Becoming Stealthier
Sophos provided details of changing tactics by Chinese APT groups over a five-year period, involving a shift towards stealthy, targeted attacks Read More