Google OSS-Fuzz Harnesses AI to Expose 26 Hidden Security Vulnerabilities
One of these flaws detected using LLMs was in the widely used OpenSSL library Read More
BianLian Ransomware Group Adopts New Tactics, Posing Significant Risk
The BianLian ransomware group has shifted exclusively to exfiltration-based extortion and is deploying multiple new TTPs for initial access and persistence Read More
Secret Service Tracking People’s Locations without Warrant
This feels important: The Secret Service has used a technology called Locate X which uses location data harvested from ordinary apps installed on phones. Because...
Lumma Stealer Proliferation Fueled by Telegram Activity
Spreading malware via Telegram channels allows threat actors to bypass traditional detection mechanisms and reach a broad, unsuspecting audience Read More
A Fifth of UK Enterprises “Not Sure” If NIS2 Applies
Over a fifth of large UK businesses aren’t sure of their compliance responsibilities under the new NIS2 directive Read More
Five Charged in Scattered Spider Case
Five men have been indicted in connection with crimes committed by the Scattered Spider group Read More
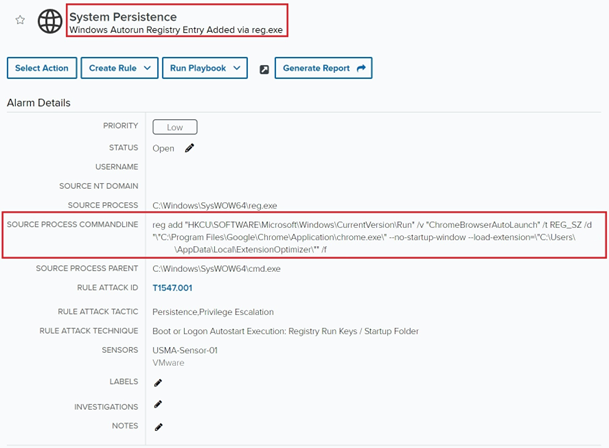
Stories from the SOC: Registry Clues to PDF Blues: A Tale of PUA Persistence
Executive Summary Establishing persistence on a system allows a threat actor continued access or process execution across system restarts or other changes. For this reason,...
Smashing Security podcast #394: Digital arrest scams and stream-jacking
In our latest episode we discuss how a woman hid under the bed after scammers told her she was under "digital arrest", how hackers are...
Five Privilege Escalation Flaws Found in Ubuntu needrestart
Five LPE flaws in Ubuntu’s needrestart utility enable attackers to gain root access in versions prior to 3.8 Read More
60% of Emails with QR Codes Classified as Spam or Malicious
60% of QR code emails are spam according findings from Cisco Talos, who also identified attackers using QR code art to bypass security filters Read...