BadUSB explained: How rogue USBs threaten your organization
In January 2022, the FBI issued a public warning over a USB attack campaign in which numerous USB drives, laced with malicious software, were sent...
Red Cross: Supply Chain Data Breach Hit 500K People
Red Cross: Supply Chain Data Breach Hit 500K People The International Committee of the Red Cross (ICRC) has revealed a major data breach that compromised the...
INTERPOL and Nigerian Police bust business email compromise ring, arrest 11
INTERPOL and the Nigerian Federal Police today announced the arrests of 11 business email compromise (BEC) actors in Nigeria as part of an international operation...
Researchers Hack Olympic Games App
Researchers Hack Olympic Games App Cybersecurity researchers in Canada have found a “devastating flaw” in the MY2022 app, designed for use by attendees of this year’s Winter...
Ransomware Attack on Moncler
Ransomware Attack on Moncler Cyber-criminals have stolen data from Italian luxury fashion brand Moncler and published it on the dark web. The maker of down jackets confirmed Tuesday that...
IRS Will Soon Require Selfies for Online Access
If you created an online account to manage your tax records with the U.S. Internal Revenue Service (IRS), those login credentials will cease to work...
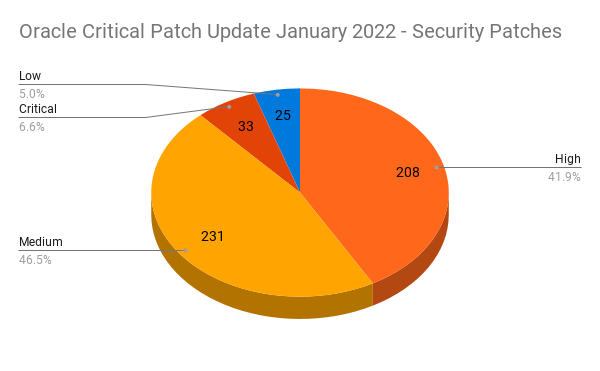
Oracle January 2022 Critical Patch Update Addresses 266 CVEs
Oracle addresses 266 CVEs in its first quarterly update of 2022 with 497 patches, including 25 critical updates. Background On January 18, Oracle released its...
Supply chain vulnerability allows attackers to manipulate SAP transport system
A supply chain vulnerability in the SAP transport system that allows attackers to infiltrate the change management or software deployment process has been identified by...
The 2021 Threat Landscape Retrospective: Targeting the Vulnerabilities that Matter Most
A review of the year in vulnerabilities and breaches, with insights to help guide cybersecurity strategy in 2022 and beyond. “We do not learn from...
The Prometheus traffic direction system is a major player in malware distribution
Cybercrime is fueled by a complex ecosystem of criminal groups that specialize on different pieces of the final attack chains experienced by victims. There are...