Zelle Is Using My Name and Voice without My Consent
Okay, so this is weird. Zelle has been using my name, and my voice, in audio podcast ads—without my permission. At least, I think it...
Supporting Your Secure Cloud Goals: Our 2023 Year in Review
2023 was a year full of efforts to help support you in meeting your secure cloud goals. Here's a look back at just a few...
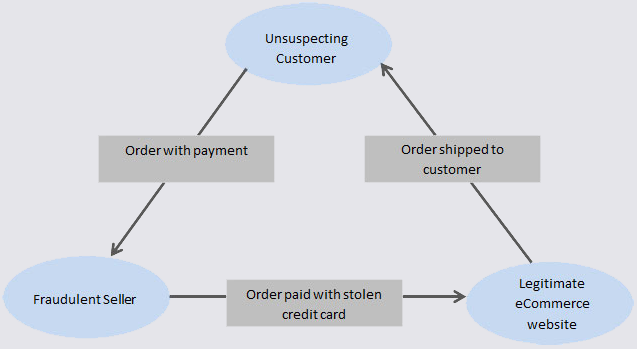
Canadian Man Stuck in Triangle of E-Commerce Fraud
A Canadian man who says he’s been falsely charged with orchestrating a complex e-commerce scam is seeking to clear his name. His case appears to...
35.5 million customers of major apparel brands have their data breached after ransomware attack
Bought some Timberland shoes? Wear a North Face jacket? You, and millions of purchasers of other popular high-street brands, could have had their data stolen...
Speaking to the CIA’s Creative Writing Group
This is a fascinating story. Last spring, a friend of a friend visited my office and invited me to Langley to speak to Invisible Ink,...
xorg-x11-server-1.20.14-30.fc39
FEDORA-2024-2815d55cdf Packages in this update: xorg-x11-server-1.20.14-30.fc39 Update description: Fix use after free related to CVE-2024-21886 Read More
Russian Coldriver Hackers Deploy Malware to Target Western Officials
Google has warned that the Russia-linked Coldriver has expanded its targeting of Western officials by deploying malware to exfiltrate sensitive data Read More
Experts Urge Clearer Direction in South Africa’s Cyber Strategy
South Africa’s cyber defenses have been lacking direction and resources for too long, researchers from the Carnegie Endowment for International Peace argued Read More
ZDI-24-075: Trend Micro Deep Security Improper Access Control Local Privilege Escalation Vulnerability
This vulnerability allows local attackers to escalate privileges on affected installations of Trend Micro Deep Security. An attacker must first obtain the ability to execute...
ZDI-24-076: Trend Micro Deep Security Link Following Local Privilege Escalation Vulnerability
This vulnerability allows local attackers to escalate privileges on affected installations of Trend Micro Deep Security. An attacker must first obtain the ability to execute...