Smashing Security podcast #306: No Fly lists, cell phones, and the end of ransomware riches?
What are prisoners getting up to with mobile phones? Why might ransomware no longer be generating as much revenue for cybercriminals? And how on earth...
DSA-5328 chromium – security update
Multiple security issues were discovered in Chromium, which could result in the execution of arbitrary code, denial of service or information disclosure. Read More
DSA-5329 bind9 – security update
Several vulnerabilities were discovered in BIND, a DNS server implementation, which may result in denial of service against named. Read More
USN-5829-1: Linux kernel (Raspberry Pi) vulnerabilities
It was discovered that the NFSD implementation in the Linux kernel did not properly handle some RPC messages, leading to a buffer overflow. A remote...
USN-5828-1: Kerberos vulnerabilities
It was discovered that Kerberos incorrectly handled certain S4U2Self requests. An attacker could possibly use this issue to cause a denial of service. This issue...
httpd-2.4.55-1.fc36
FEDORA-2023-6d4055d482 Packages in this update: httpd-2.4.55-1.fc36 Update description: new version 2.4.55 Read More
httpd-2.4.55-1.fc37
FEDORA-2023-f6ff3f85eb Packages in this update: httpd-2.4.55-1.fc37 Update description: new version 2.4.55 Read More
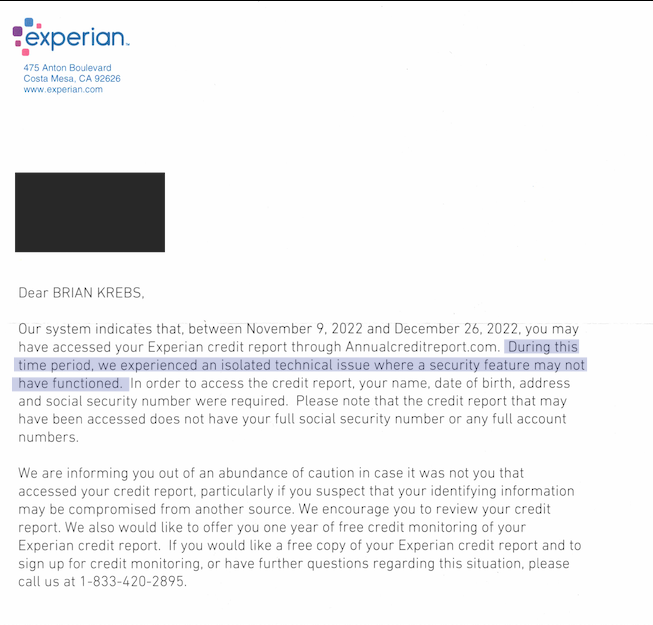
Experian Glitch Exposing Credit Files Lasted 47 Days
On Dec. 23, 2022, KrebsOnSecurity alerted big-three consumer credit reporting bureau Experian that identity thieves had worked out how to bypass its security and access...
Attackers move away from Office macros to LNK files for malware delivery
For years attackers have used Office documents with malicious macros as one of the primary methods of infecting computers with malware. Microsoft finally took steps...
North Korean Group TA444 Shows ‘Startup’ Culture, Tries Numerous Infection Methods
The threat actor has been targeting cryptocurrency exchanges since at least 2017 Read More