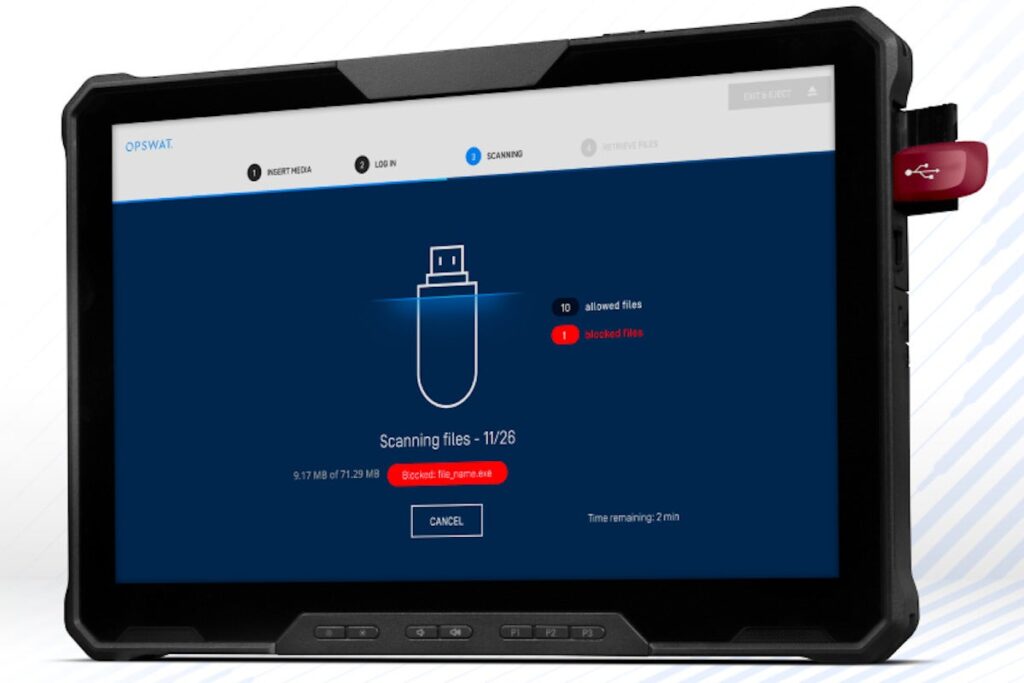
OPSWAT mobile hardware offers infrastructure security for the air gap
Infrastructure protection vendor OPSWAT has announced the availability of its new MetaDefender Kiosk K2100 hardware, designed to provide a mobile option for users who want...
Microsoft attributes Charlie Hebdo attacks to Iranian nation-state threat group
Microsoft’s Digital Threat Analysis Center (DTAC) has attributed a recent influence operation targeting the satirical French magazine Charlie Hebdo to an Iranian nation-state actor. Microsoft...
Attacking Machine Learning Systems
The field of machine learning (ML) security—and corresponding adversarial ML—is rapidly advancing as researchers develop sophisticated techniques to perturb, disrupt, or steal the ML model...
The ethics of biometric data use in security
The content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information...
Stalkerware Developer Hit with $400K Fine
New York attorney general says software facilitates domestic abuse Read More
USN-5842-1: EditorConfig Core C vulnerability
Mark Esler and David Fernandez Gonzalez discovered that EditorConfig Core C incorrectly handled memory when handling certain inputs. An attacker could possibly use this issue...
Legacy VMware Bug Exploited in Global Ransomware Campaign
Vendor's ESXi hypervisors are being targeted Read More
Will your incident response team fight or freeze when a cyberattack hits?
If there’s an intrusion or a ransomware attack on your company, will your security team come out swinging, ready for a real fight? CISOs may...
Scam Alert for Dingo Token That Charges 99% Fee
Crypto has a market cap of close to $11m Read More
ZDI-23-094: Netatalk dsi_writeinit Heap-based Buffer Overflow Remote Code Execution Vulnerability
This vulnerability allows remote attackers to execute arbitrary code on affected installations of Netatalk. Authentication is not required to exploit this vulnerability. Read More