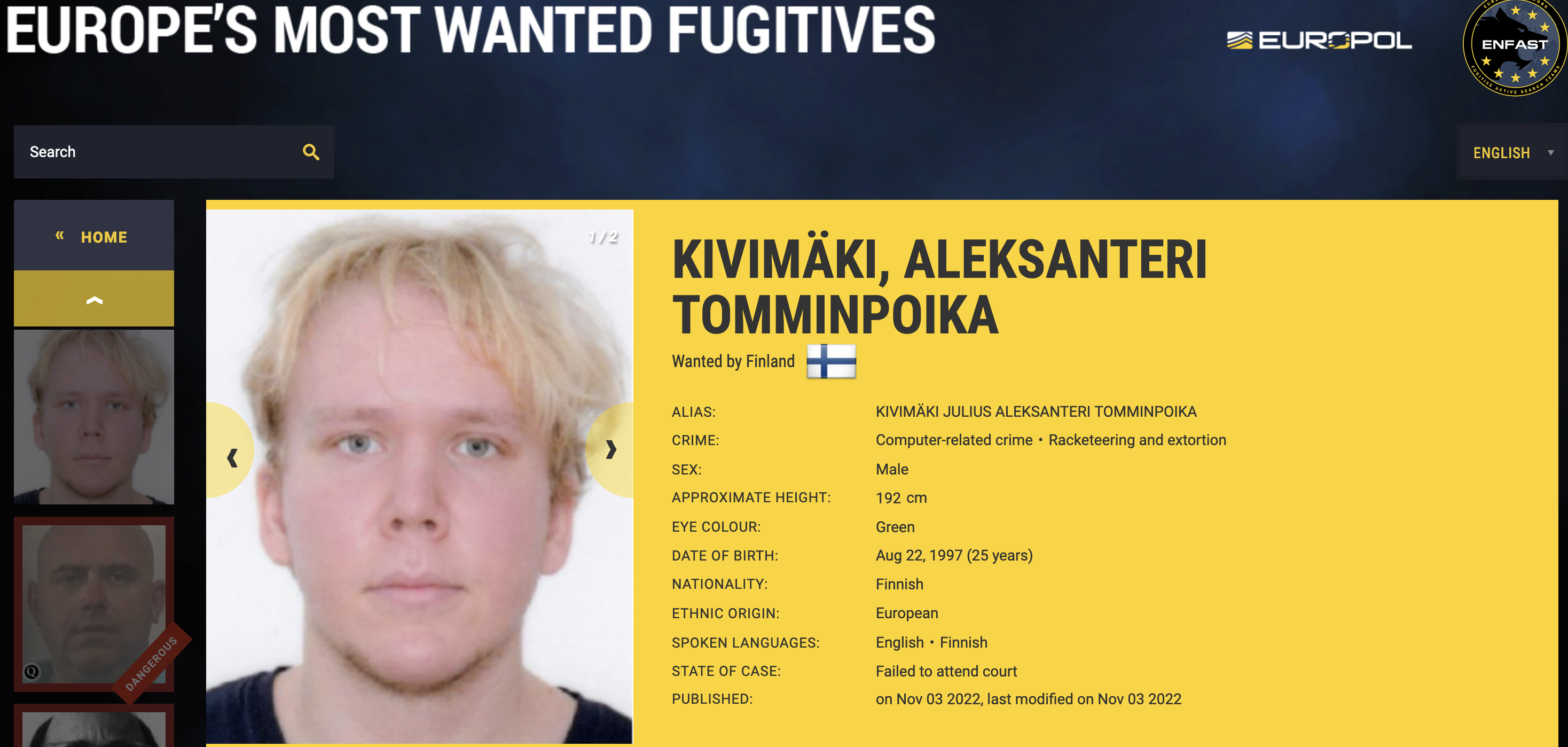
Prosecutors in Finland this week commenced their criminal trial against Julius Kivimäki, a 26-year-old Finnish man charged with extorting a once popular and now-bankrupt online psychotherapy practice and thousands of its patients. In a 2,200-page report, Finnish authorities laid out how they connected the extortion spree to Kivimäki, a notorious hacker who was convicted in 2015 of perpetrating tens of thousands of cybercrimes, including data breaches, payment fraud, operating a botnet and calling in bomb threats.
In November 2022, Kivimäki was charged with attempting to extort money from the Vastaamo Psychotherapy Center. In that breach, which occurred in October 2020, a hacker using the handle “Ransom Man” threatened to publish patient psychotherapy notes if Vastaamo did not pay a six-figure ransom demand.
Vastaamo refused, so Ransom Man shifted to extorting individual patients — sending them targeted emails threatening to publish their therapy notes unless paid a 500-euro ransom. When Ransom Man found little success extorting patients directly, they uploaded to the dark web a large compressed file containing all of the stolen Vastaamo patient records.
Security experts soon discovered Ransom Man had mistakenly included an entire copy of their home folder, where investigators found many clues pointing to Kivimäki’s involvement. By that time, Kivimäki was no longer in Finland, but the Finnish government nevertheless charged Kivimäki in absentia with the Vastaamo hack. The 2,200-page evidence document against Kivimäki suggests he enjoyed a lavish lifestyle while on the lam, frequenting luxury resorts and renting fabulously expensive cars and living quarters.
But in February 2023, Kivimäki was arrested in France after authorities there responded to a domestic disturbance call and found the defendant sleeping off a hangover on the couch of a woman he’d met the night before. The French police grew suspicious when the 6′ 3″ blonde, green-eyed man presented an ID that stated he was of Romanian nationality.
A redacted copy of an ID Kivimaki gave to French authorities claiming he was from Romania.
Finnish prosecutors showed that Kivimäki’s credit card had been used to pay for the virtual server that hosted the stolen Vastaamo patient notes. What’s more, the home folder included in the Vastaamo patient data archive also allowed investigators to peer into other cybercrime projects of the accused, including domains that Ransom Man had access to as well as a lengthy history of commands he’d executed on the rented virtual server.
Some of those domains allegedly administered by Kivimäki were set up to smear the reputations of different companies and individuals. One of those was a website that claimed to have been authored by a person who headed up IT infrastructure for a major bank in Norway which discussed the idea of legalizing child sexual abuse.
Another domain hosted a fake blog that besmirched the reputation of a Tulsa, Okla. man whose name was attached to blog posts about supporting the “white pride” movement and calling for a pardon of the Oklahoma City bomber Timothy McVeigh.
Kivimäki appears to have sought to sully the name of this reporter as well. The 2,200-page document shows that Kivimäki owned and operated the domain krebsonsecurity[.]org, which hosted various hacking tools that Kivimäki allegedly used, including programs for mass-scanning the Internet for systems vulnerable to known security flaws, as well as scripts for cracking database server usernames and passwords, and downloading databases.
Ransom Man inadvertently included a copy of his home directory in the leaked Vastaamo patient data. A lengthy history of the commands run by that user show they used krebsonsecurity-dot-org to host hacking and scanning tools.
Mikko Hyppönen, chief research officer at WithSecure (formerly F-Secure), said the Finnish authorities have done “amazing work,” and that “it’s rare to have this much evidence for a cybercrime case.”
Petteri Järvinen is a respected IT expert and author who has been following the trial, and he said the prosecution’s case so far has been strong.
“The National Bureau of Investigation has done a good job and Mr Kivimäki for his part some elementary mistakes,” Järvinen wrote on LinkedIn. “This sends an important message: online crime does not pay. Traces are left in the digital world too, even if it is very tedious for the police to collect them from servers all around the world.”
Antti Kurittu is an information security specialist and a former criminal investigator. In 2013, Kurittu worked on an investigation involving Kivimäki’s use of the Zbot botnet, among other activities Kivimäki engaged in as a member of the hacker group Hack the Planet (HTP). Kurittu said it remains to be seen if the prosecution can make their case, and if the defense has any answers to all of the evidence presented.
“Based on the public pretrial investigation report, it looks like the case has a lot of details that seem very improbable to be coincidental,” Kurittu told KrebsOnSecurity. “For example, a full copy of the Vastaamo patient database was found on a server that belonged to Scanifi, a company with no reasonable business that Kivimäki was affiliated with. The leaked home folder contents were also connected to Kivimäki and were found on servers that were under his control.”
The Finnish daily yle.fi reports that Kivimäki’s lawyers sought to have their client released from confinement for the remainder of his trial, noting that the defendant has already been detained for eight months.
The court denied that request, saying the defendant was still a flight risk. Kivimäki’s trial is expected to continue until February 2024, in part to accommodate testimony from a large number of victims. Prosecutors are seeking a seven-year sentence for Kivimäki.