Authored by: Lakshya Mathur and Yashvi Shah
As the Back-to-School season approaches, scammers are taking advantage of the opportunity to deceive parents and students with various scams. With the increasing popularity of online shopping and digital technology, people are more inclined to make purchases online. Scammers have adapted to this trend and are now using social engineering tactics, such as offering high discounts, free school kits, online lectures, and scholarships, to entice unsuspecting individuals into falling for their schemes.
McAfee Labs has found the following PDFs targeting back-to-school trends. This blog is a reminder for parents on what to educate their children on and how not to fall victim to such fraud.
Fake captcha PDFs campaign
McAfee Labs encountered a PDF file campaign featuring a fake CAPTCHA on its first page, to verify human interaction. The second page contained substantial content on back-to-school advice for parents and students, giving the appearance of a legitimate document. These tactics were employed to make the PDF seem authentic, entice consumers to click on the fake CAPTCHA link, and evade detection.
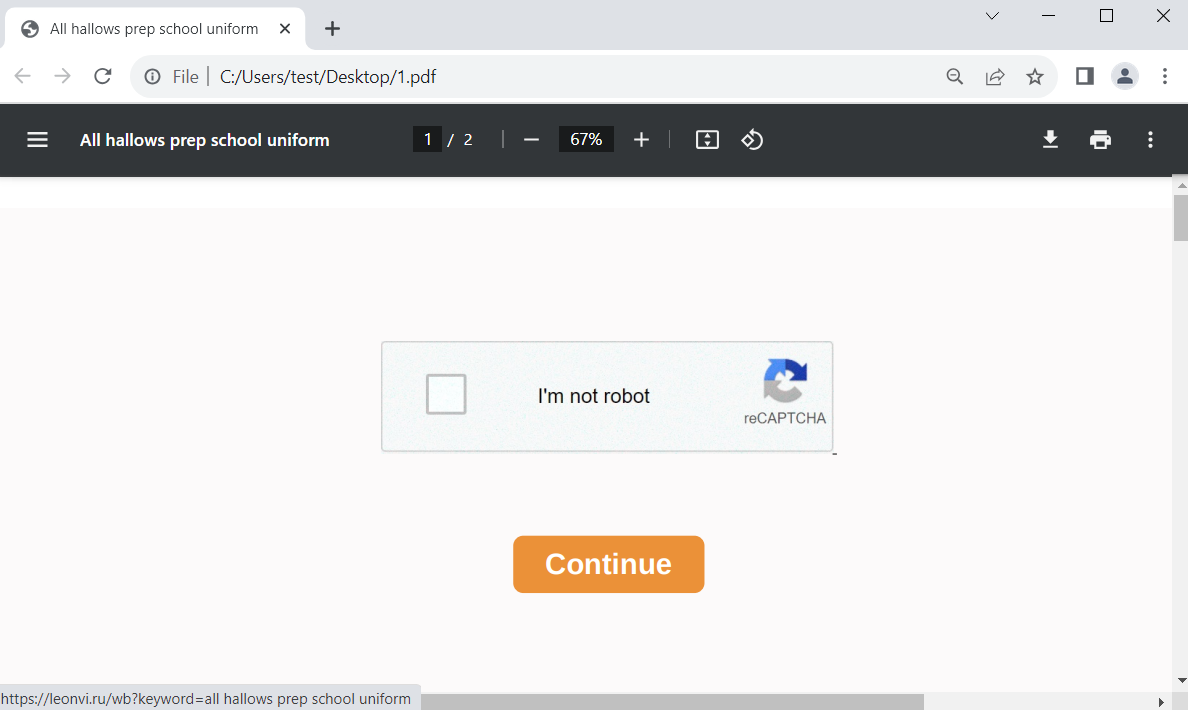
Figure 1 – Fake CAPTCHA and scammy link
Figure 2 – PDF Second Page
Figure 3 – Zoomed in content from Figure 2
As shown in Figure 1, there is a fake captcha image that, when clicked, redirects to a URL displayed at the bottom left of the figure. This URL has a Russian domain and goes through multiple redirections before reaching its destination. The scam URL contains the text “all hallows prep school uniform,” and leads to a malicious site that sets cookies, monitors user behavior, and collects interactions, sending the data to servers owned by the domain’s operators.
Figures 2 and 3 display the second page of the PDF, designed to appear legitimate to users and spam and security scanners.
In this campaign, we identified a total of 13 domains, with 11 being of Russian origin and 2 from South Africa. You can find the complete list of these domains in the final IOC (Indicators of Compromise) section.
All domains were created in 2020 and 2021 and use Cloudflare’s name servers.
Geographical Distribution
These domains were discovered operating worldwide, targeting consumers across various countries. The United States and India stood out as the top countries where users were most often targeted.
Figure 4 – Geographical distribution of all the scam domains
What more to expect?
As the season begins, the scenario is only the beginning of back-to-school scam season. Parents and students should remain vigilant against fraud, such as:
Shopping scams: During back-to-school season, scammers employ various tactics: setting up fake online stores offering discounted school supplies, uniforms, and gadgets, but delivering substandard or nonexistent products; spreading fraudulent social media ads with enticing deals that lead to fake websites collecting personal information and payment details; and sending fake package delivery emails, tricking recipients into clicking on malicious links to perform phishing and malware attacks.
Tax/Loan free scams: Scammers target students and parents with student loan forgiveness scams, offering false debt reduction programs in exchange for upfront payments or personal information. They also entice victims with fake scholarships or grants, prompting fees or sensitive data, while no genuine assistance exists. Unsolicited calls from scammers posing as government agencies or loan providers add to the deception, using high-pressure tactics to extract personal information or immediate payments.
Identity theft: Scammers employ various identity theft tactics to exploit students and parents: attempting unauthorized access to school databases for personal information, creating fake enrollment forms to collect sensitive data, and sending phishing emails posing as educational institutions or retailers to trick victims into sharing personal information or login credentials.
Deepfake AI Voice scams: Scammers might use deepfake AI technology to create convincing voice recordings of school administrators, teachers, or students. They can pose as school officials to deceive parents into making urgent payments or sharing personal information. Additionally, scammers might mimic students’ or teachers’ voices to solicit fraudulent fundraisers for fake school programs or claim that students have won scholarships or prizes to trick them into paying fees or revealing sensitive information. These scams exploit the trust and urgency surrounding back-to-school activities.
How to Stay Protected?
Be skeptical, if something appears to be too good to be true, it probably is.
Exercise caution when registering or sharing personal information on questionable sites.
Stay informed about these scams to safeguard yourself
Maintain a skeptical approach towards unsolicited calls and emails.
Keep your anti-virus and web protection up to date and perform regular full scans on your devices.
IOC (Indicator of Compromise)
Filetype/URL
Value
PDF
474987c34461cb4bd05b81d040cae468ca5b88e891da4d944191aa819a86ff21
426ad19eb929d0214254340f3809648cfb0ee612c8374748687f5c119ab1a238
5cb6ecc4af42075fa822d2888c82feb2053e67f77b3a6a9db6501e5003694aba
Domain
traffine[.]ru
leonvi[.]ru
trafffi[.]ru
norin[.]co[.]za
gettraff[.]ru
cctraff[.]ru
luzas.yubit[.]co[.]za
ketchas[.]ru
maypoin[.]ru
getpdf.pw
traffset[.]ru
jottigo[.]ru
trafffe[.]ru
The post The Season of Back to School Scams appeared first on McAfee Blog.