CVE-2021-33589
Ribose RNP before 0.15.1 does not implement a required step in a cryptographic algorithm, resulting in weaker encryption than on the tin of the algorithm....
#CYBERUK23: Five Takeaways From the NCSC Conference on the UK’s Cyber Strategy
More collaboration, both with the private sector and international allies, is at the top of the list in the UK’s cyber playbook Read More
Good Friday Agreement paved way for Northern Ireland’s emergence as a global cybersecurity hub
The Belfast (Good Friday) Agreement played an integral role in enabling Northern Ireland’s growth as a global cybersecurity hub, according to UK government chiefs speaking...
Most interesting products to see at RSA Conference 2023
Security professionals attending this year’s RSA Conference expect to learn about new tools, platforms, and services from the 600-plus vendors exhibiting there. That’s a lot...
3CX hack highlights risk of cascading software supply-chain compromises
At the end of March, an international VoIP software company called 3CX with over 600,000 business customers suffered a serious software supply-chain compromise that resulted...
Government Agencies Release Blueprint for Secure Smart Cities
NCSC and CISA want to balance connectivity with resilience Read More
The strong link between cyber threat intelligence and digital risk protection
While indicators of compromise (IoCs) and attackers’ tactics, techniques, and processes (TTPs) remain central to threat intelligence, cyber threat intelligence (CTI) needs have grown over...
China Developing Anti-Satellite Weapons – Report
Pentagon leak reveals US concerns over technology push Read More
Capita: Data Was Taken in March Cyber Incident
IT outsourcer claims customer, employee and supplier info may be at risk Read More
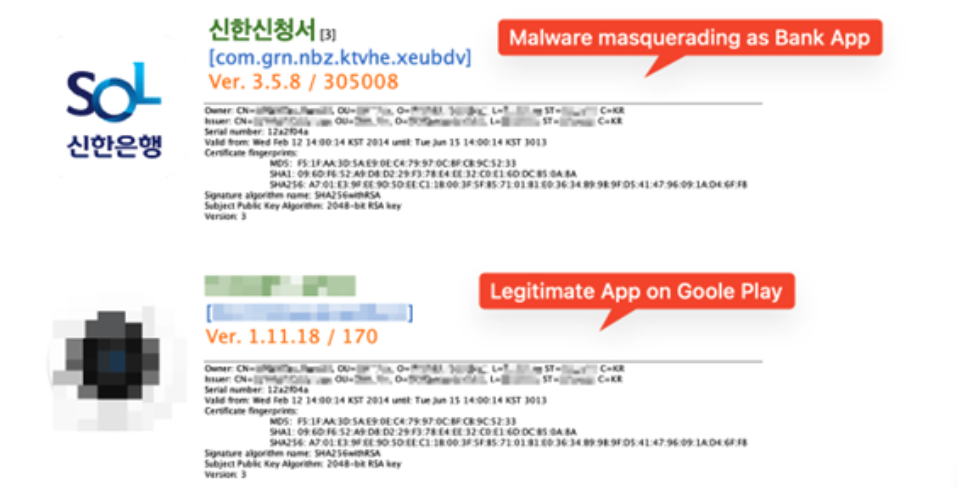
Fakecalls Android Malware Abuses Legitimate Signing Key
Authored by Dexter Shin McAfee Mobile Research Team found an Android banking trojan signed with a key used by legitimate apps in South Korea last...