CVE-2022-0194
This vulnerability allows remote attackers to execute arbitrary code on affected installations of Netatalk. Authentication is not required to exploit this vulnerability. The specific flaw...
USN-5980-1: Linux kernel vulnerabilities
It was discovered that the System V IPC implementation in the Linux kernel did not properly handle large shared memory counts. A local attacker could...
google-guest-agent-20230221.00-2.fc39
FEDORA-2023-ffa2112211 Packages in this update: google-guest-agent-20230221.00-2.fc39 Update description: Automatic update for google-guest-agent-20230221.00-2.fc39. Changelog * Tue Mar 28 2023 Major Hayden <major@redhat.com> - 20230221.00-2 - Bump...
Multiple Vulnerabilities in Apple Products Could Allow for Arbitrary Code Execution
Multiple vulnerabilities have been discovered in Apple Products, the most severe of which could allow for arbitrary code execution. Safari is a graphical web browser...
MS-ISAC CYBERSECURITY ADVISORY – Multiple Vulnerabilities in Adobe Products Could Allow for Arbitrary Code Execution
Multiple vulnerabilities have been discovered in Adobe products, the most severe of which could allow for arbitrary code execution. Multiple vulnerabilities have been discovered in...
Multiple Vulnerabilities in Google Chrome Could Allow for Arbitrary Code Execution
Multiple vulnerabilities have been discovered in Google Chrome, the most severe of which could allow for arbitrary code execution. Google Chrome is a web browser...
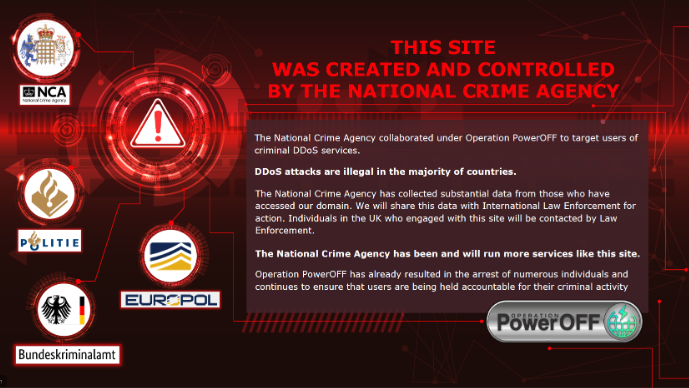
UK Sets Up Fake Booter Sites To Muddy DDoS Market
The United Kingdom’s National Crime Agency (NCA) has been busy setting up phony DDoS-for-hire websites that seek to collect information on users, remind them that...
Hackers changed tactics, went cross-platform in 2022, says Trend Micro
Payouts from ransomware victims declined by 38% in 2022, prompting hackers to adopt more professional and corporate tactics to ensure higher returns, according to Trend...
Clipboard-Injector Attacks Target Cryptocurrency Users
The malware campaign relying on this technique was observed abusing Tor Browser installers Read More
USN-5979-1: Linux kernel (HWE) vulnerabilities
It was discovered that the KVM VMX implementation in the Linux kernel did not properly handle indirect branch prediction isolation between L1 and L2 VMs....