CISA orders federal agencies to catalog their networks, and scan for bugs
You always want to know what is attached to your network. And whether it could be vulnerable or not. Read more in my article on...
Dell launches new cybersecurity resources to enhance zero-trust adoption, cyber resilience
Dell Technologies has announced a raft of new cybersecurity resources to help customers simplify zero-trust adoption and improve their cyber resiliency. These include a new...
Malicious Tor Browser Installers Spread Via Darknet Video on YouTube
The malicious variant distributed spyware to collect personal data and send it to the hacker Read More
USN-5653-1: Django vulnerability
Benjamin Balder Bach discovered that Django incorrectly handled certain internationalized URLs. A remote attacker could possibly use this issue to cause Django to crash, resulting...
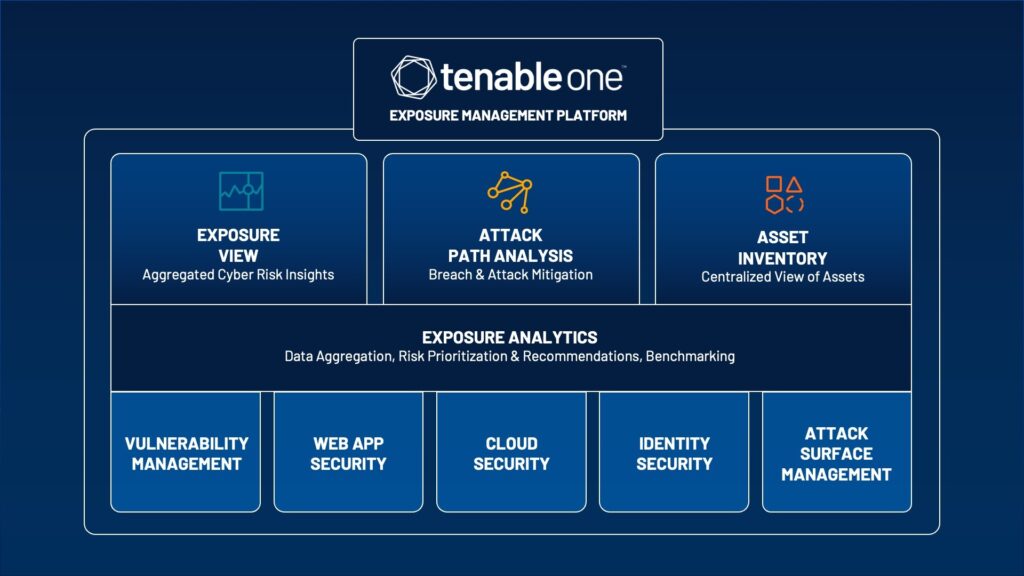
Introducing the Tenable One Exposure Management Platform
Anticipate likely attacks. Proactively reduce your exposure. Communicate with your key stakeholders. Today, Tenable is proud to announce the Tenable One Exposure Management Platform, which...
Exposure Management: Reducing Risk in the Modern Attack Surface
Cybersecurity organizations struggle with reactive and siloed security programs and with a sprawl of point tools that generate heaps of fragmented data but few insights....
NSA Employee Charged with Espionage
An ex-NSA employee has been charged with trying to sell classified data to the Russians (but instead actually talking to an undercover FBI agent). It’s...
Kolide can help you nail audits and compliance goals with endpoint security for your entire fleet
Graham Cluley Security News is sponsored this week by the folks at Kolide. Thanks to the great team there for their support! Do you know...
Bug Exploitation Now Top Ransomware Access Vector
Secureworks also warns of rise of info-stealers Read More
8 Cybersecurity trends to be aware of in 2022/2023
This blog was written by an independent guest blogger. The last couple of months were devastating for cybersecurity. Cyber threats intensify each waking day, and...