What Are Tailgating Attacks and How to Protect Yourself From Them
Whether you’re spending time on the web or working in the office, you want peace of mind knowing that you are in a safe environment....
Guide: Protecting Your Digital Identity
People in their 20s and 30s are losing it online. And by it, I mean money—thanks to digital identity theft. In its simplest form, your digital identity is made...
How to Tell Whether a Website Is Safe or Unsafe
It’s important to know that not all websites are safe to visit. In fact, some sites may contain malicious software (malware) that can harm your...
“This Connection Is Not Private” – What it Means and How to Protect Your Privacy
Have you ever been browsing online and clicked a link or search result that took you to a site that triggers a “your connection is...
pypy3.7-7.3.9-4.3.7.fc35
FEDORA-2022-01d5789c08 Packages in this update: pypy3.7-7.3.9-4.3.7.fc35 Update description: Backport fix for CVE-2021-28861 Read More
With Conti gone, LockBit takes lead of the ransomware threat landscape
The number of ransomware attacks observed over the previous three months declined compared to the previous quarter, according to reports from two threat intelligence companies....
CVE-2020-9285 (one_firmware)
Some versions of Sonos One (1st and 2nd generation) allow partial or full memory access via attacker controlled hardware that can be attached to the...
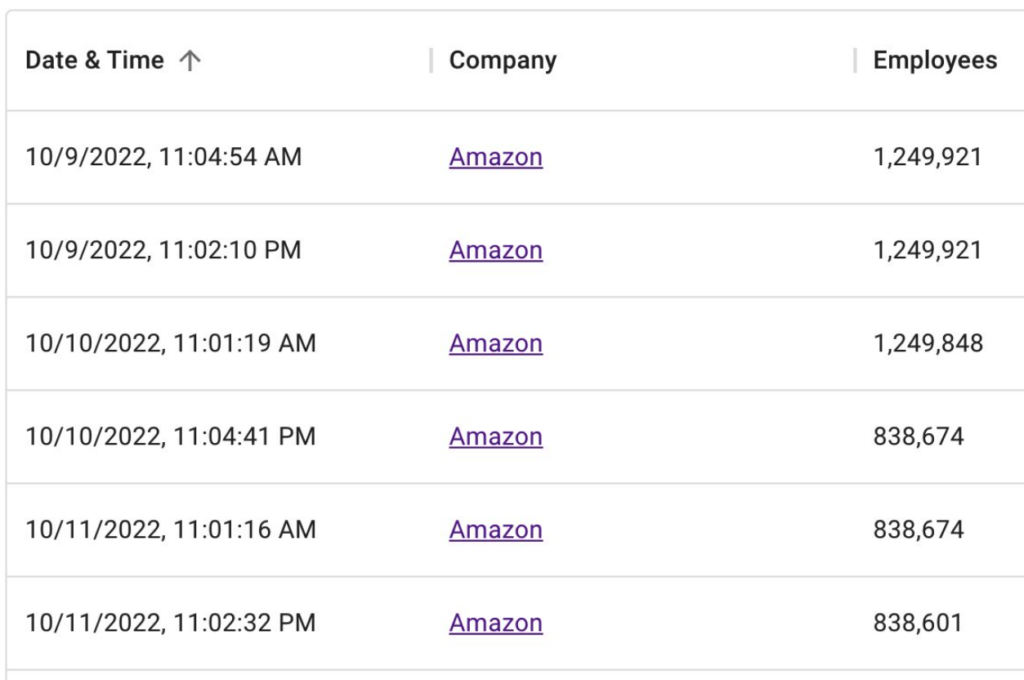
Battle with Bots Prompts Mass Purge of Amazon, Apple Employee Accounts on LinkedIn
On October 10, 2022, there were 576,562 LinkedIn accounts that listed their current employer as Apple Inc. The next day, half of those profiles no...
Ransomware is Being Used As a Precursor to Physical War: Ivanti
The data also shows ransomware groups continuing to grow in volume and sophistication Read More
Cybersecurity Workforce Gap Grows by 26% in 2022
What are the factors behind this stark rise, and how can the skills gap be closed? Read More