Anticipate likely attacks. Proactively reduce your exposure. Communicate with your key stakeholders.
Today, Tenable is proud to announce the Tenable One Exposure Management Platform, which unifies a variety of data sources into a single exposure view to help organizations gain visibility, prioritize efforts and communicate cyber risks.
Tenable One combines broad vulnerability coverage — spanning IT assets, cloud resources, containers, web apps and identity systems — and builds on the speed and breadth of vulnerability data from Tenable Research. Tenable One offers cybersecurity teams a contextual view of all assets and associated software vulnerabilities, configuration vulnerabilities and entitlement vulnerabilities, whether on-premises or in the cloud, to help them understand where they are most exposed to risk.
To say that the attack surface is growing is an understatement. A Microsoft Risk IQ study released in April found that every minute over 117,00 new hosts are created, 613 new domains are added and 375 new threats are released. Plus, the number of new vulnerabilities continues to grow – with 12,380 new CVEs published in the first half of 2022, a 31% jump over the 9,420 published in the same period last year. To combat this problem, the average large organization uses more than 130 different cybersecurity point solutions, each with its own analytics, and no consistent reporting. All of these tools can lead to duplicate and ineffective programs, with no clear path forward to tangibly reduce risk or succinctly communicate an organization’s security status.
The Tenable One Exposure Management Platform helps to eliminate the noise by bringing an organization’s entire attack surface — whether on-premises or in the cloud — into a single, unified view. This helps security leaders, practitioners and incident responders reduce the risk of an attack by drawing upon the industry’s largest vulnerability management data set and analyzing it in the context of the relationships between assets, exposures, privileges and threats across attack paths.
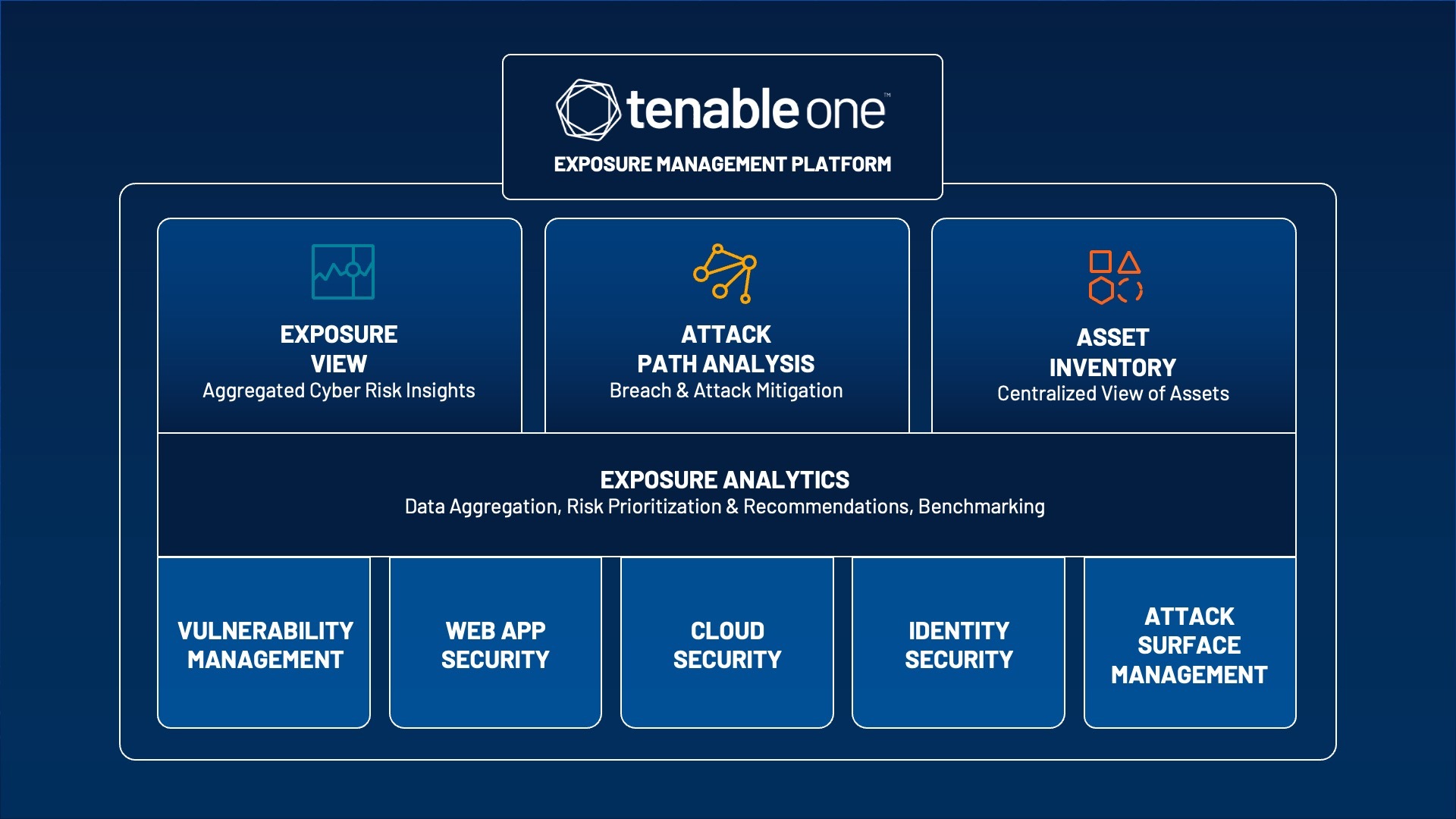
What’s inside the Tenable One Exposure Management Platform?
The Tenable One Exposure Management Platform is built on a foundation of six existing Tenable products:
Tenable Lumin
Tenable.io Vulnerability Management
Tenable.io Web Application Scanning
Tenable.cs Cloud Security
Tenable.ad Active Directory Security
Tenable.asm Attack Surface Management
Providing flexibility in deployment, it comes in two versions — Standard and Enterprise. Tenable One Enterprise Edition adds attack path analysis and attack surface management functionality to the Standard Edition.
Tenable One aggregates the cyber risk analytics data derived from each of these products and analyzes it to provide three types of insights:
cyber risk guidance: in the form of exposure views;
breach and attack mitigation via attack path analysis; and
a centralized view of assets in a comprehensive asset inventory.
Source: Tenable, October 2022
The Tenable One Exposure Management Platform provides the following key benefits:
Comprehensive visibility: Tenable One helps cybersecurity teams gain a unified view of all assets and associated software vulnerabilities, configuration vulnerabilities and entitlement vulnerabilities, whether on-premises or in the cloud, to allow them to understand where they are exposed to risk. It also continuously monitors the internet to rapidly discover and identify all external-facing assets to eliminate areas of known and unknown security risk. This helps reduce the time and effort required to understand the complete attack surface, eliminate blind spots, and build a baseline for effective risk management.
Predict and prioritize:The platform helps security leaders anticipate the consequences of a cyberattack by drawing upon the industry’s largest data set and combining it with an understanding of the relationships between assets, exposures, privileges and threats across an attack path. Tenable One significantly improves cyber risk prioritization to help cybersecurity teams continuously identify and focus on the exploitable attack and breach pathways that create the most risk. This provides more accurate and predictive remediation insights to eliminate windows of risk with the least amount of effort to help prevent attacks.
Effectively communicate cyber risk: Tenable One provides security executives and business leaders with a centralized and business-aligned view of cyber risk, with clear key performance indicators (KPIs) to show progress over time and benchmarking to compare against external peers. The platform provides actionable insights into an organization’s overall cyber risk, as well as the ability to drill into departmental or operational units. This delivers accurate business-aligned cyber risk assessments to improve overall communication and collaboration among different constituencies, which saves time, improves investment decisions, supports insurability and drives improvement over time — all while tangibly reducing risk to the organization.
Source: Tenable, October 2022
As the above image shows, exposure views provide a unified global exposure score drawn from a variety of different data sources. They enable focused security efforts through clear, concise insight into an organization’s security exposure — enabling security pros to answer such critical questions as:
how secure are we?;
where do we stand in our preventative and mitigation efforts?; and
how are we doing over time and what are the key events?
Tenable One supports a wide range of users
Security practitioners and managers will have full visibility into their attack surface, along with a unified view of all assets. They will be able to prioritize their efforts in remediating software, configuration and entitlement vulnerabilities. Such comprehensive visibility and prioritization enables security teams to understand their attack surface as the attackers see it, eliminate blind spots and build a baseline for effective risk management while improving decision making.
Security managers and incident response teams can use Tenable One’s contextual view of threats, assets and privileges to focus available resources on their organization’s most pressing security needs. Such focus will help these teams eliminate windows of risk and efficiently allocate resources to remediate and respond. Tenable One allows IR teams to anticipate the consequences of an attack by giving them a contextual understanding of the relationships between assets, users and privileges across the entire attack surface. The clear and easily communicated KPIs provided by Tenable One offer insights into progress over time and provide benchmarked comparisons within the organization.
CISOs, business information security officers (BISOs) and security executives require accurate risk assessments to improve investment decisions, evaluate insurability, meet regulatory and compliance requirements and drive organizational improvement. Tenable One provides these executives with actionable metrics they can use to measure, compare and communicate cyber risk to non-technical execs and operating teams. A unified view of cyber risk with clear KPIs allows executives to measure progress over time and make benchmarked comparisons against industry peers and within the organization. The goal? To help security leaders answer the question “how secure are we?”
One important point for Tenable.ep customers: With the launch of Tenable One, you will be automatically upgraded to Tenable One Standard Edition at no additional cost. With this upgrade, you can continue to take full advantage of all capabilities in Tenable.ep today, plus Exposure View and Asset Inventory available in Tenable One. Please reach out to your Tenable representative for more information.
Learn more
Read the blog, Exposure Management: Reducing Risk in the Modern Attack Surface
Download the white paper, 3 Real-World Challenges Facing Cybersecurity Leaders: How an Exposure Management Platform Can Help
Visit the Tenable One product page, https://www.tenable.com/products/tenable-one