Friday Squid Blogging: Piglet Squid
Nice article on the piglet squid. As usual, you can also use this squid post to talk about the security stories in the news that...
MoonBounce UEFI implant used by spy group brings firmware security into spotlight
Researchers uncovered a stealthy UEFI rootkit that's being used in highly targeted campaigns by a notorious Chinese cyberespionage group with suspected government ties. The group...
A Backdoor in WordPress AccessPress Plugins and Themes Could Allow an Attacker Access to a Targeted Website
A backdoor has been discovered in WordPress AccessPress plugins and themes, which could allow an attacker access to a targeted website. AccessPress plugins and themes...
Attackers use public cloud providers to spread RATs
A campaign that uses public cloud service providers to spread malware has been discovered by Cisco Talos. The offensive is the latest example of threat...
Homelife of Connecticut Residents Secretly Recorded
Homelife of Connecticut Residents Secretly Recorded A man from Connecticut has been arrested on suspicion of using digital devices to record his neighbors. Waterford resident Keith Hancock...
Pennsylvania Approves Ransomware Bill
Pennsylvania Approves Ransomware Bill Pennsylvania has approved new legislation barring state and local governments from using taxpayers’ money to pay ransoms to cyber-criminals. Senate Bill 726,...
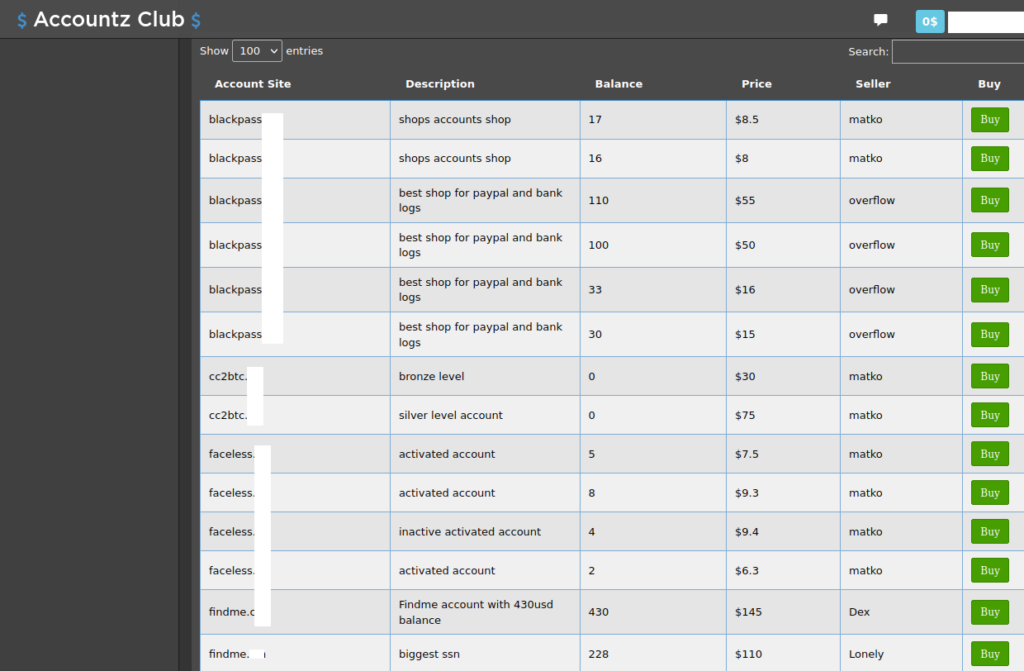
Crime Shop Sells Hacked Logins to Other Crime Shops
Up for the “Most Meta Cybercrime Offering” award this year is Accountz Club, a new cybercrime store that sells access to purloined accounts at services...
Memorial Health System Confirms Data Breach
Memorial Health System Confirms Data Breach A cyber-attack on an Ohio-based health system may have exposed the protected health information (PHI) of 216,478 patients. Memorial Health System was...
China’s Olympics App Is Horribly Insecure
China is mandating that athletes download and use a health and travel app when they attend the Winter Olympics next month. Citizen Lab examined the...
Multiple Vulnerabilities in Cisco Products Could Allow for Arbitrary Code Execution
Multiple vulnerabilities have been discovered in Cisco Products, the most severe of which could allow for arbitrary code execution. Successful exploitation of the most severe...